Lookout Discovers Massistant Chinese Mobile Forensic Tooling


- Massistant is the presumed successor to Chinese forensics tool, “MFSocket”, reported in 2019 and attributed to publicly traded cybersecurity company, Meiya Pico
- The forensics tool works in tandem with a corresponding desktop software.
- Massistant gains access to device GPS location data, SMS messages, images, audio, contacts and phone services.
- Meiya Pico maintains partnerships with domestic and international law enforcement partners, both as a surveillance hardware and software provider, as well as through training programs for law enforcement personnel.
- Travel to and within mainland China carries with it the potential for tourists, business travelers, and persons of interest to have their confidential mobile data acquired as part of lawful intercept initiatives by state police.
Researchers at the Lookout Threat Lab have discovered a mobile forensics application named Massistant, used by law enforcement in China to collect extensive information from mobile devices. This application is believed to be the successor to a previously reported forensics tool named “MFSocket” used by state police and reported by various media outlets in 2019. These samples require physical access to the device to install, and were not distributed through the Google Play store.
Forensics tools are used by law enforcement personnel to collect sensitive data from a device confiscated by customs officials, at local or provincial border checkpoints or when stopped by law enforcement officers.
These tools can pose a risk to enterprise organizations with executives and employees that travel abroad - especially to countries with border patrol policies that allow them to confiscate mobile devices for a short period of time upon entry. In 2024, the Ministry of State Security introduced new legislation that would allow law enforcement personnel to collect and analyze devices without a warrant. There have been anecdotal reports of Chinese law enforcement collecting and analyzing the devices of business travellers. In some cases, researchers have discovered persistent, headless surveillance modules on devices confiscated and then returned by law enforcement such that mobile device activity can continue to be monitored even after the device has been returned.
Massistant: A Successor to Meiya Pico’s MFSocket
In June 2019, a Chinese journalist named Muyi Xiao, published a since-deleted Twitter thread discussing a new mobile surveillance tool that was being discussed on Chinese social media platforms. According to Xiao, a number of Chinese netizens claimed an application named “MFSocket” had been installed on their mobile devices by police officers. Xiao attributed this surveillance tool to a publicly traded Chinese technology company, Xiamen Meiya Pico Information Co., Ltd. (厦门市美亚柏科信息股份有限公司).
Following this, cybersecurity researcher Baptiste Robert (also known as @fs0c131y) publicly shared his analysis of the application in June 2019. In this report he noted the use of signing certificates that listed Meiya Pico as the developer of the MFSocket application. These details seemed to confirm Xiao’s assertion.
Since this reporting, Lookout researchers have uncovered a related forensics application named “Massistant”, which we believe to be a successor to MFSocket. These samples were acquired between mid-2019 and early 2023 and are predominantly signed with an Android signing certificate referencing Meiya Pico.
Chinese Q&A forums return a number of references to an application of the same name that users claim was installed on their devices by police services in a similar manner to MFSocket.
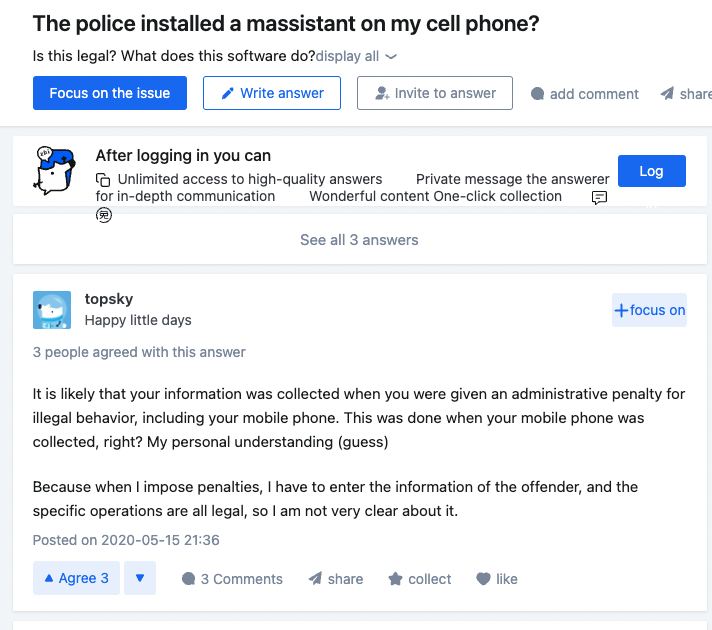
These forum posts date back to mid-2020, which seems to support the hypothesis that this tool was introduced to replace the MFSocket mobile component in Meiya Pico’s “Mobile Master” ecosystem.
According to one user on Zhidao, the Ministry of Public Security (国家公安部) website claims it is illegal to uninstall the software, although Lookout researchers have not found a reference to Massistant on the Ministry of Public Security website.
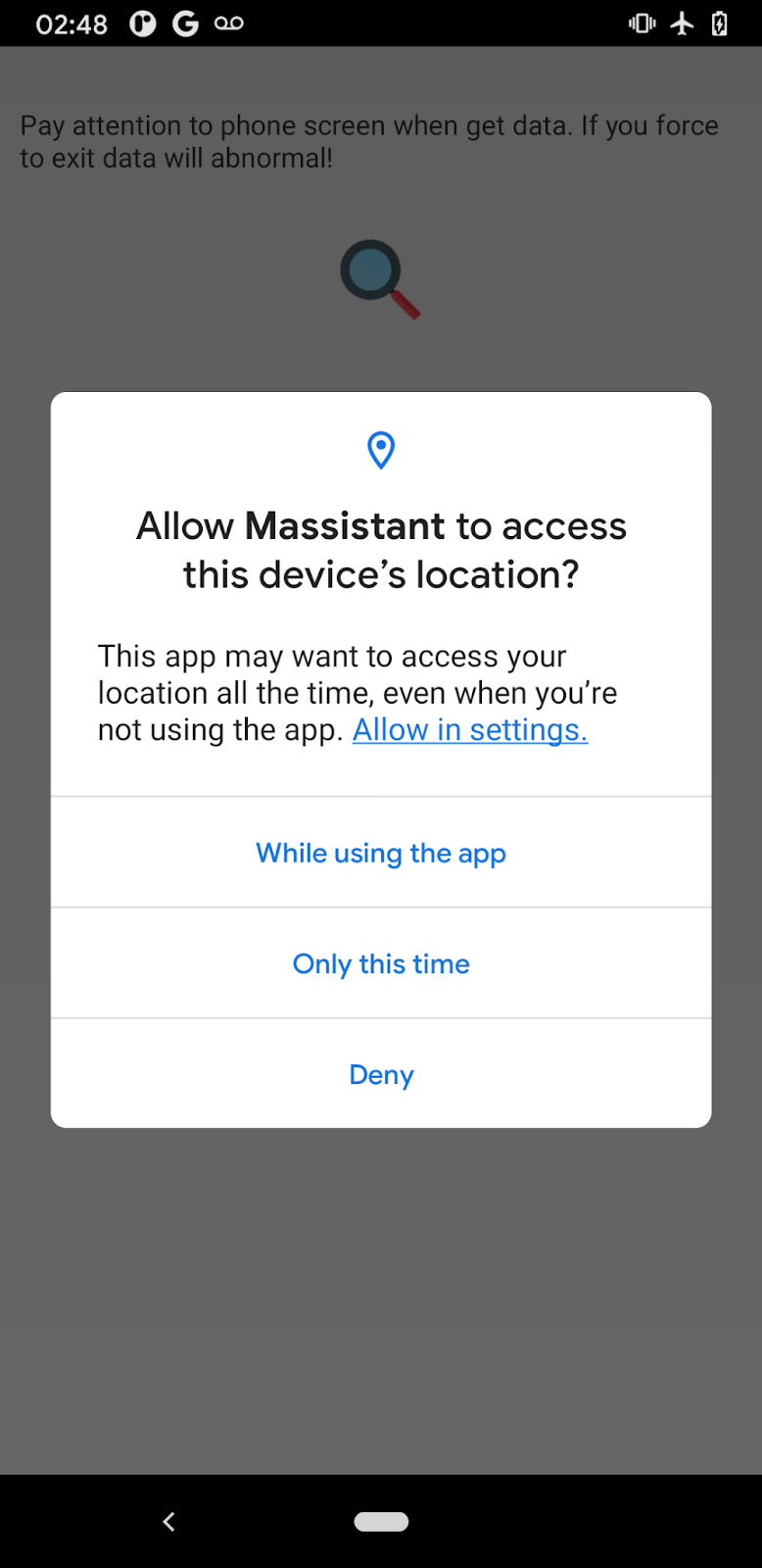
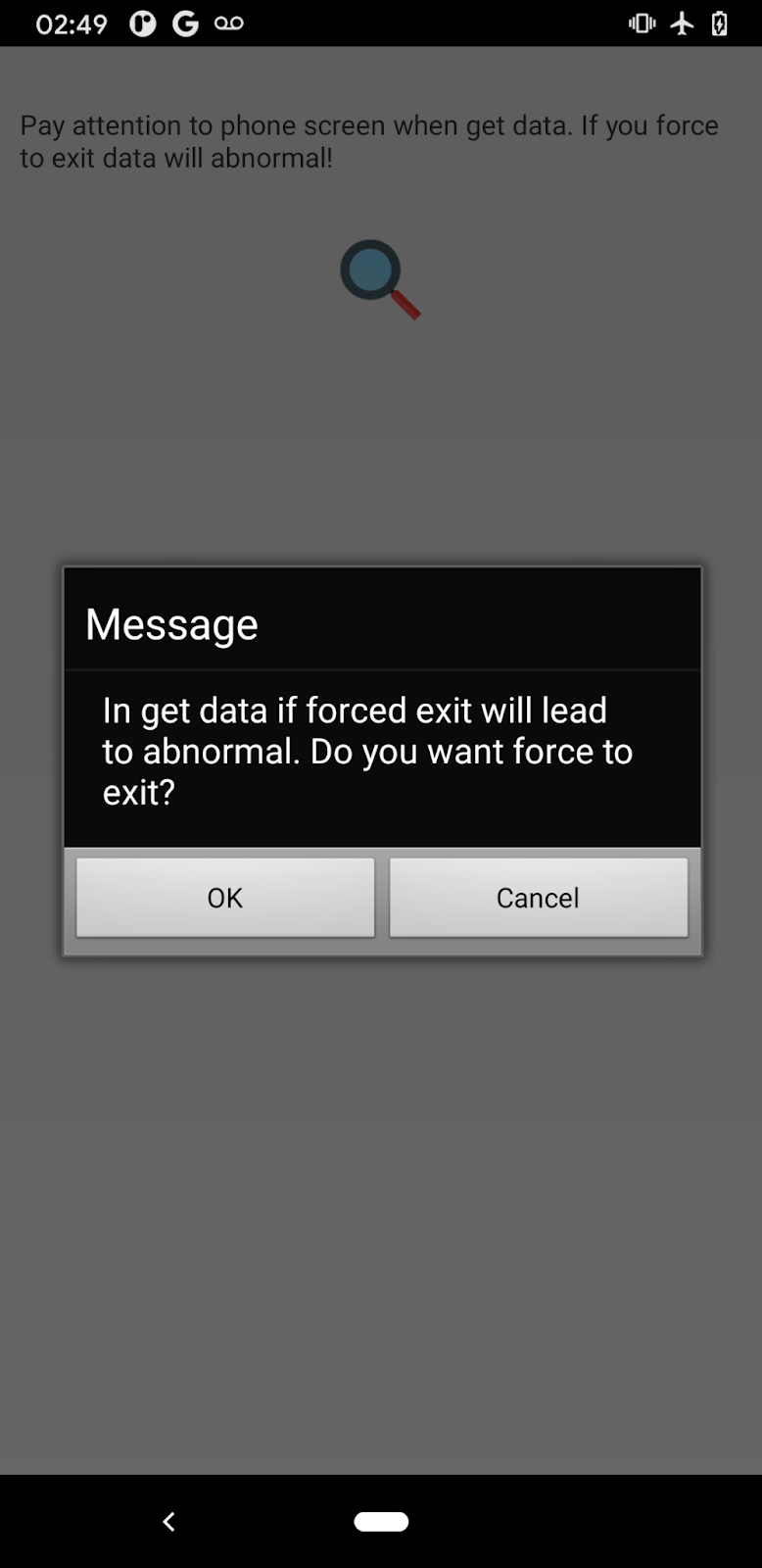
Like MFSocket, Massistant is intended to work in tandem with a desktop forensics software to extract data from a compromised device. As such, the forensics tool does not connect to a server, rather to localhost over the same port as MFSocket, port 10102. It is likely that the desktop component is facilitating communication with the compromised device through a port forwarding service, like those offered by the Android Debug Bridge.
When launched, the user is prompted to approve a series of permission requests for access to device GPS location data, SMS messages, images, audio, contacts and phone services. No other interaction is required; if the user attempts to exit the application they receive a notice that the application is in “get data” mode and exiting would result in some error. This message is translated to only two languages: Chinese (Simplified characters) and “US” English.
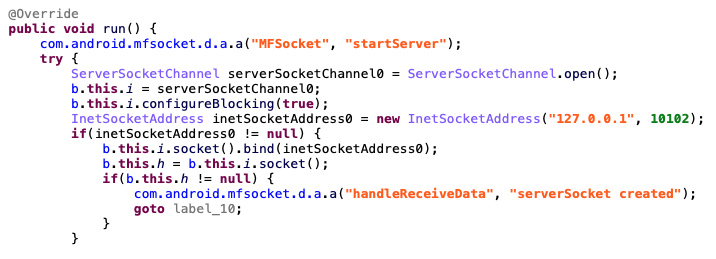
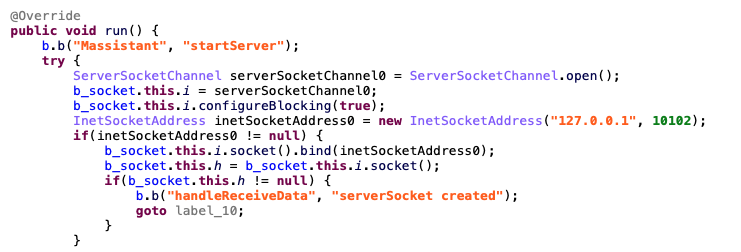
In addition to the same port reference, Massistant and MFSocket share a number of other similarities. A significant overlap in their code is apparent, with Massistant existing as a clear iteration upon the older MFSocket version 5.0 application, and they have been assigned identical application icons. Furthermore, many of the commands found in early MFSocket versions have been included in Massistant


In most cases, where both applications share functionality, their classes are identical. In addition, Massisstant contains an XML resource file named “mfsocket.xml”.
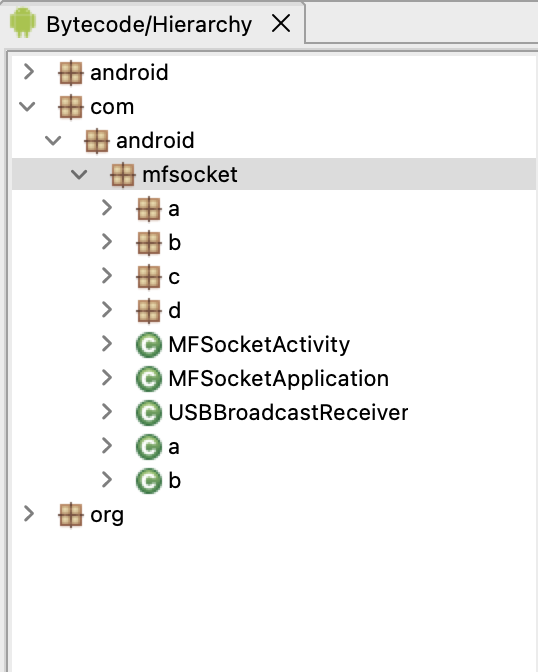
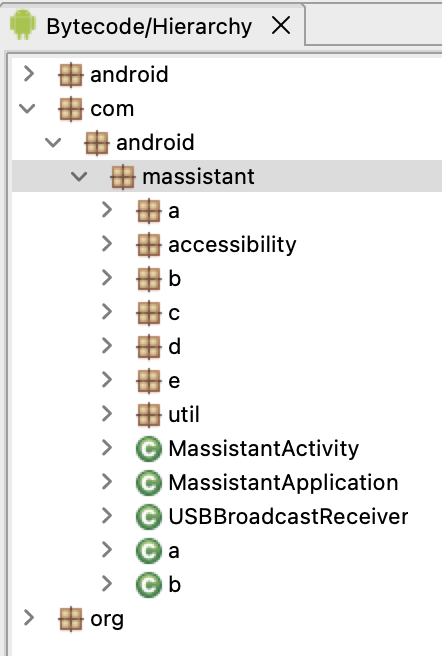
While at this time it does not appear that Massistant is capable of exfiltrating data from a device once it leaves the presence of its desktop counterpart, its existence on a device and any logging details or data files would indicate to a device owner that their mobile device data had been compromised if it was confiscated.
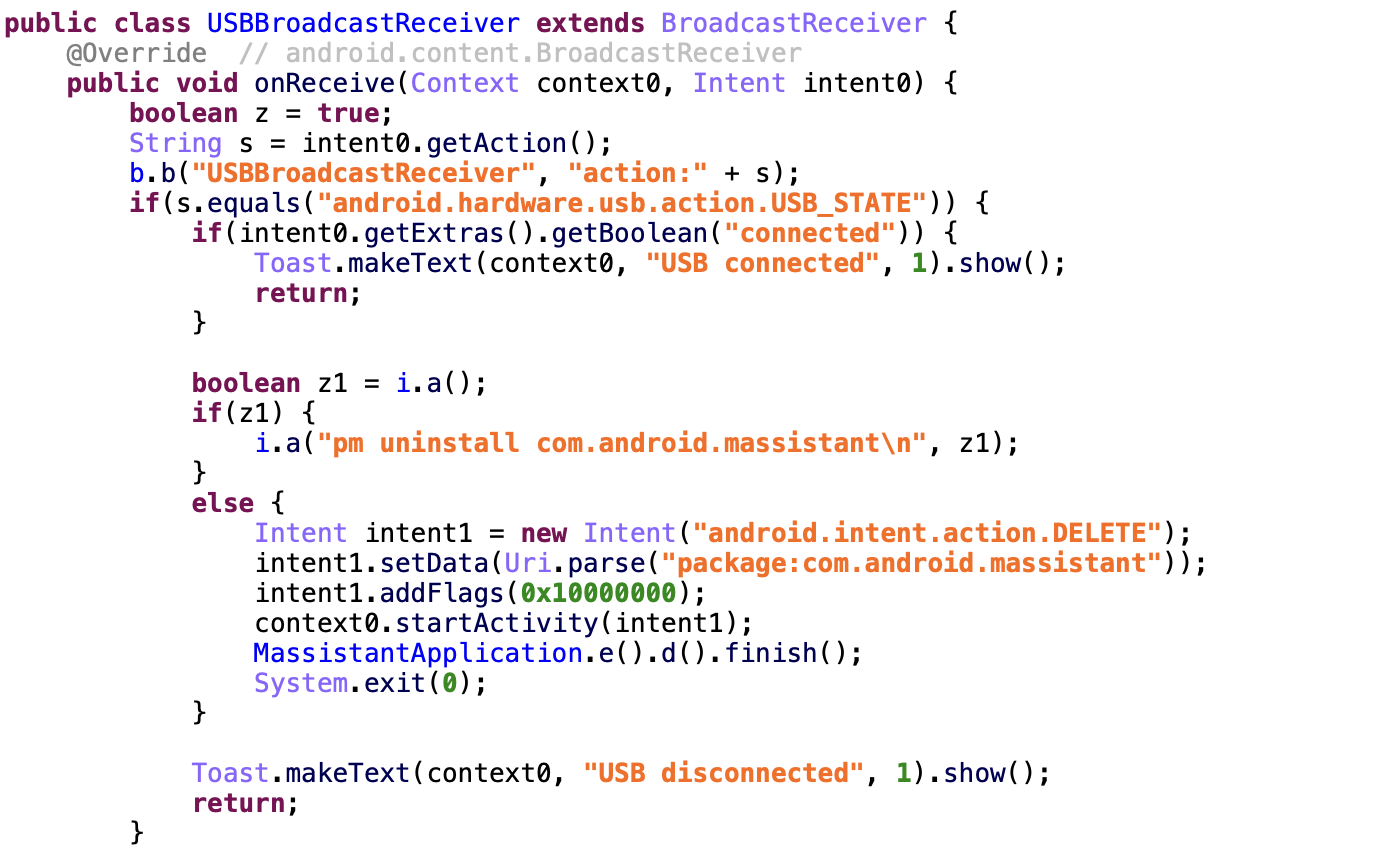
Like MFSocket, Massistant uses a USBBroadcastReceiver to uninstall itself from the device when it is disconnected from USB. Presumably, there have been cases where this has failed and resulted in Chinese-speaking netizens discovering an additional application on their device following its confiscation by Chinese authorities.
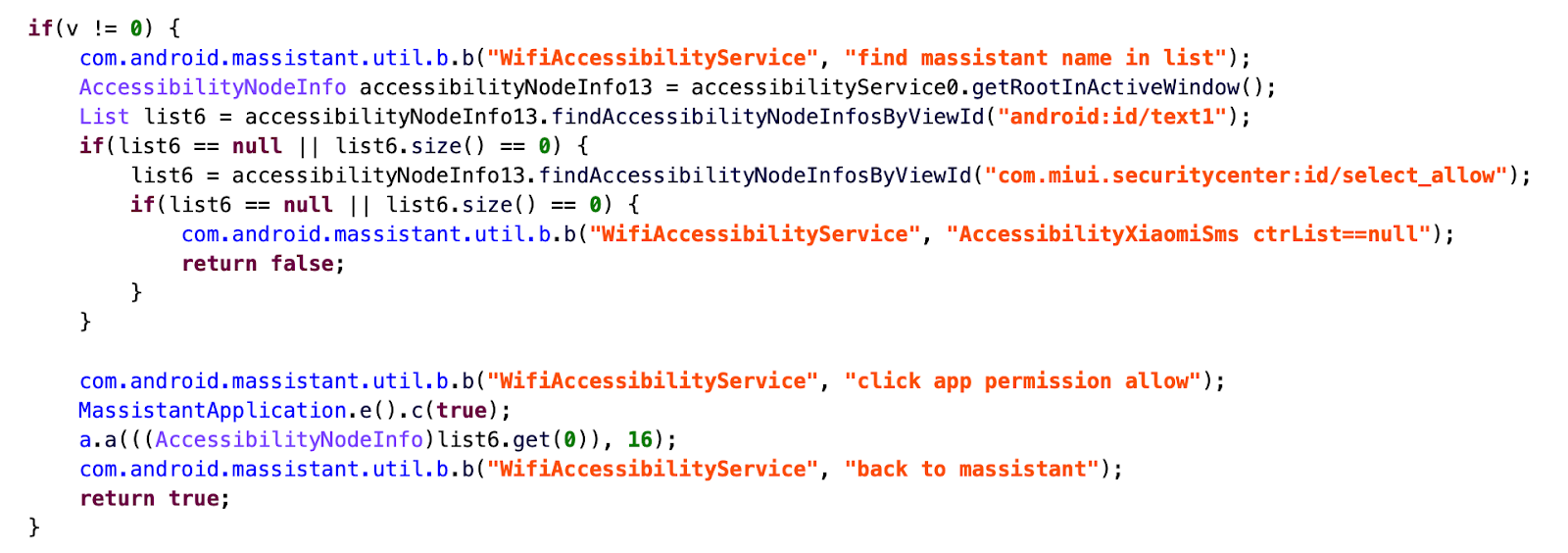
The new Massistant application introduces a number of additional functions to the MFSocket feature set. AccessibilityServices are introduced through a series of classes referred to by Meiya Pico developers as “AutoClick” – an attempt to automatically bypass conditions in certain device security applications, such as automatically allowing Massistant to run when prompted by the Miui Security Center tool.
The latest version of Massistant, v. 8.5.7, also introduces the ability to connect to a confiscated device using the Android Debug Bridge over WiFi and to download additional files to the device. This functionality is implemented in a native library named libNativeUtil.so. An announcement on the Meiya Pico Chinese language commercial website referenced a further update to this feature for the Mobile Master Series of products in May 2024, however Lookout researchers have not yet encountered an updated version of the Massistant client.
Massistant also introduces additional support for third party messaging applications. The original MFSocket collected application data from Telegram; Massistant has augmented this capability to collect messaging data from Signal and Letstalk.
The MFSocket and Meiya Pico Connection
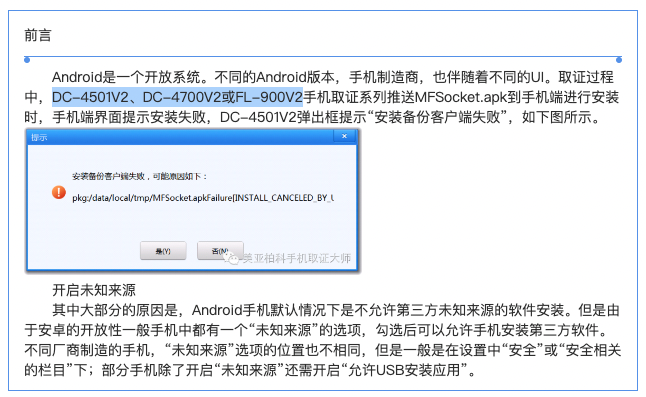
During her investigation, Xiao uncovered a guide published by Meiya Pico. The guide reads, “During the evidence collection process…the DC-4501V2, DC-4700V2 or FL-900V2 mobile phone evidence collection series pushes MFSocket.apk to the mobile phone for installation…”. These version codes refer to the second iteration of a tool advertised as the “Meiya Pico Mobile Master Series” on the Chinese language Meiya Pico website, 300188[.]cn. The commercial website is named for the company’s stock exchange code on the Shenzhen Stock Exchange (300188). The company also offers an English and Russian-language website at meiyapico[.]com.

In April 2020, Meiya Pico issued a statement on their website announcing the discontinuation of upgrades to the DC-4500/DC-4501V1, DC-4700V1 and FL-900V1 products and a forthcoming replacement suite of tooling with the same product names, upgraded from the V2 mentioned in the guide shared by Xiao to V3. Lookout researchers assess with low confidence that it is around this time that MFSocket was replaced with Massistant.
Xiamen Meiya Pico Information Co., Ltd.
Xiamen Meiya Pico Information Co., Ltd. (“Meyia Pico” is a publicly traded Chinese technology company that controls roughly 40% of the digital forensics market share in mainland China.
In December 2023, Meiya Pico changed its name to SDIC Intelligence Xiamen Information Co., Ltd. (国投智能(厦门)信息股份有限公司). However, signing certificates for MFSocket and Massistant, reference Meiya Pico as the software’s development organization.
Journalists have frequently reported on Meiya Pico’s involvement in the Chinese commercial surveillance market, with their tooling used by law enforcement and the surveillance of minority groups in the region. In April 2025, researchers at Turquoise Roof released a report detailing the company’s procurement of training and tooling for the Tibet Police College in Lhasa.
Meiya Pico themselves frequently advertise their involvement in both Chinese and international law enforcement product exhibitions, including INTERPOL World Exhibition. In fact, Meiya Pico boasts partnerships with a number of international government clients, including the Russian military who have purchased its forensics and mobile surveillance products.
As of 2018, it was reported that the military investigative directorate of the Russian Federation’s Investigative Committee (военное следственное управление Следственного Комитета РФ) purchased two Meiya Pico products, iDC-8811 Forensic Magicube V3 and iDC-4501 Mobile Forensics System V2 through a forensics contractor, “ExpertExpress LLC”. These two products, along with Cellebrite’s IFM-2008 Forensics Master suite, were purchased for 5 million rubles (approximately $74,000USD) in 2018. The Russian purchase was intended to enable Russian military criminal investigations, and does not appear targeted toward foreign victims.
However, the Russian purchase was most likely later annulled, as the selling company, ExpertExpress and its subcontractor Ester Solutions sold the Meiya Pico solutions to the Russian military’s Investigative Committee using falsified licenses. In October 2018, the owner of Ester Solutions, Dmitriy Saturchenko, was arrested under large-scale fraud charges.
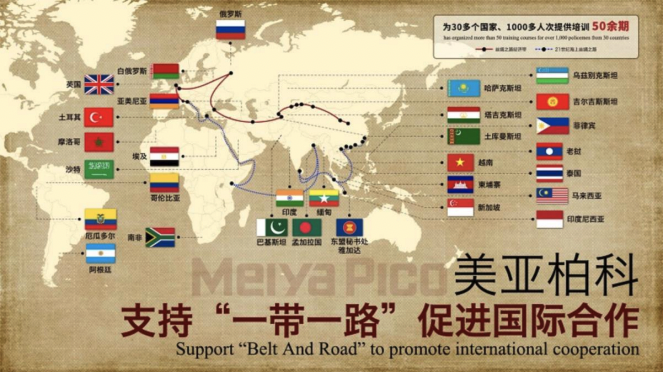
Meiya Pico has also been instructed by China’s Ministry of Public Security to train representatives from countries affiliated with the Belt & Road Initiative in digital forensics investigations. As of September 2019, 29 countries were referenced as participants in this initiative.
In 2021, Meiya Pico was sanctioned by the United States Government Office of Foreign Assets Control under program CMIC-EO13959, “Chinese Military Companies Sanctions”. Its stated goal is listed as, "Addressing the Threat From Securities Investments That Finance Communist Chinese Military Companies”.
Conclusion
Travel to and within mainland China carries with it the potential for tourists, business travelers, and persons of interest to have their confidential mobile data acquired as part of lawful intercept initiatives by state police. Lookout customers are protected from both MFSocket and Massistant. Please contact us here if you believe your device may have been compromised.
Indicators of Compromise
SHA1
895ad87f382de53f7323117b47150eaf0550cbf4
7a6d81b19425d985270121c46368c9ac12ed1b26
14c29a0e44076c88b177193650a9d4567291d0ea
256c357f884f33c032d2352ee6ff73fe94da83a8
91a6e8769be93f625f239f9c8bad82545c936f20
ceb3b0c6dc703c76d274f4862d98b4f054536518
66ef2c18178d8988a210d09b17f3b23394306b40
4cc68d1538c372a31d2989e04f1c0726a66ebb7a
e5d4685ceedc44184ae0d249269a94018c88a4ff
0275f283ce280f717a2674d82aaf1cb562c3b90c
215bd2972c5598787addad911915b9a04932d68d
990004827ec2b08b52afd0df5750cfed502dbc1c
df4c8bccadf71d5c29a7a92d40fee4629fe7a384
93c5cd3a0bb04012927ccd29e505772492fcfbee
8659920f99a96c294c9857a761ce0729f3a8f2f7
71fc752af7d108b7aede7d17ec7dae3a9cbb3470
4b30d1d9d4a1e4571d4cd7aaeb91aee192a7a512
1c6e67c6f1c9b6a332d844b772af3ef9e5e8d8dd
f22eea7248d023f74f631a8812115bf4981df2e7
2458fa6f7b0faf662a940ab92a1f144b2c384ce4
f514f711b4b83d3cf2a4b4c602483a120b448f63
7ec4f46df0bb9fca801719b7f67f642bdd0a9e97
c17e9325a6932ff8b725b18e4ddcb6dadab99457
Authors


Identify and Prevent Threats with Lookout Threat Advisory
Stop Cyberattacks Before They Start With Industry-Leading Threat Intelligence.
Lookout Threat Advisory offers advanced mobile threat intelligence, leveraging millions of devices in our global network and top security research insights to protect your organization.



