Stop Social Engineering Before It Starts
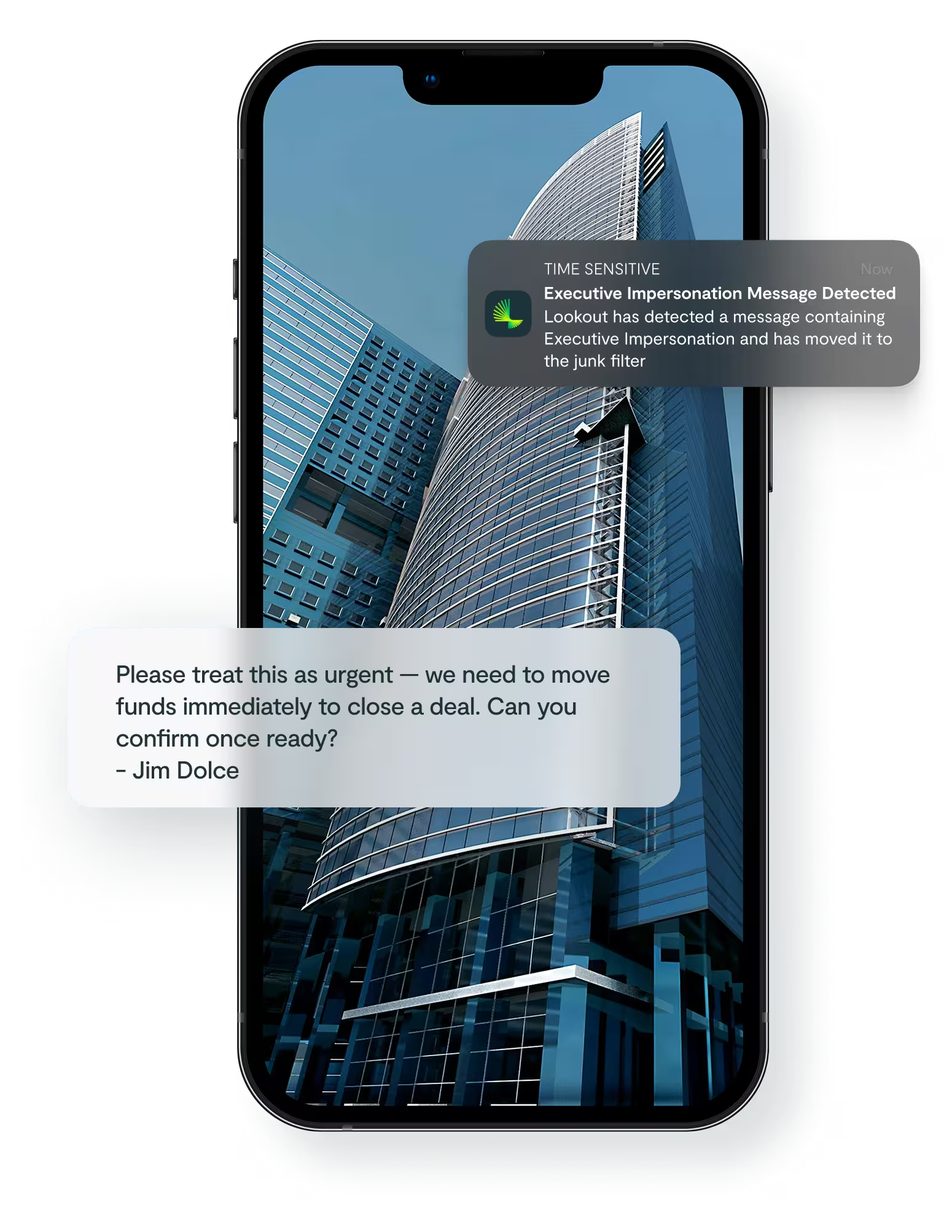
Executive impersonation is a targeted form of social engineering where attackers pose as high-ranking company leaders—such as a CEO, CFO, or VP—to deceive employees into taking harmful actions. These attacks often occur through SMS and messaging apps where adversaries exploit the authority and urgency associated with executive requests to pressure employees into making costly mistakes—such as wiring funds or sharing sensitive information.
By understanding communication patterns and identifying anomalies, Lookout prevents attackers from exploiting authority, urgency, and trust to manipulate employees into sharing credentials, transferring funds, or bypassing normal procedures. Whether your workforce is on managed smartphones or BYOD devices, Lookout ensures consistent protection across your mobile ecosystem—before damage can occur.
The High-stakes risk of executive impersonation.
Executive impersonation isn’t just another phishing tactic—it’s a calculated abuse of trust, authority, and timing. These attacks bypass traditional defenses and rely on social engineering to manipulate employees into taking high-risk actions, often without realizing they’ve been deceived.


Industry-first visibility and actionable reporting.
Executive impersonation attacks span every industry, department, and level of the organization—yet most security teams lack visibility into when, where, and how often they occur. Traditional tools struggle to detect these socially engineered threats, especially when messages contain no links or attachments.
With Lookout, you see the whole picture. In addition to detecting and blocking executive impersonation attempts, Lookout provides industry-first reporting that uncovers critical insights—such as attack frequency, message content, targeted users, and attacker behavior—giving organizations the intelligence needed to stay ahead of evolving threats. Key capabilities include:
- Real-time alerting and detailed event data in the Lookout console
- Correlation of sender identity, phishing payloads, device data, and attack timelines
- Intent-based detection of smishing attacks, blocking malicious messages even when no links or attachments are present
- Seamless integration into SIEM, SOAR, and XDR platforms
- Customizable user education prompts triggered during active threats
By uncovering behavioral patterns, target profiles, and frequency trends, Lookout equips security teams to detect the early stages of coordinated impersonation campaigns—and take proactive action before any damage is done.
Hands-on labs: Master mobile threat defense with us.

New to the team, not to risk—protect them from day one.
New employees are prime targets for executive impersonation attacks, often due to their limited familiarity with internal processes and leadership. Lookout’s executive impersonation protection identifies and blocks these threats early—before attackers can exploit a new hire’s inexperience. By proactively monitoring communication channels and leveraging advanced machine learning, Lookout helps organizations safeguard new team members from day one, reducing risk while reinforcing a culture of security.
Prevent urgent-text scams targeting vulnerable employees.
Attackers often impersonate C-level executives via SMS to send urgent requests for wire transfers or financial approvals—specifically targeting assistants and finance teams. Lookout stops these sophisticated smishing attacks with behavioral analysis and intent-based detection, preventing employees from acting on fraudulent messages. The result: high-value targets stay protected, and your organization avoids costly breaches to its finances and reputation.

Experience executive impersonation protection for yourself.
User and admin setup experiences

End user experience with custom messaging










