Executive Summary: Mobile Risk Has Become a Persistent Baseline
Building on the findings from the Q2 2025 Mobile Threat Landscape Report, Q3 2025 marks the point where mobile risk stops being a transitional security challenge and becomes a structural enterprise exposure.
Mobile devices now operate as permanent, high-trust access points into identity, cloud, and business workflows—meaning elevated mobile exposure is no longer episodic or situational, but a sustained condition embedded in how modern enterprises function.
As a result, mobile risk has settled into a persistent, elevated baseline across enterprise environments, reshaping the organization’s overall attack surface and redefining where initial compromise, identity abuse, and data exposure now begin.
Threat actors are no longer probing whether mobile-first techniques are effective. Instead, they are executing repeatable, scalable campaigns that rely on mobile phishing, social engineering, and identity abuse as primary access vectors. In many cases, attackers no longer require malware or vulnerability exploitation at the outset; instead, they operate entirely within legitimate authentication and access workflows.
This shift reflects broader changes in how enterprises operate. Mobile devices now serve as primary interfaces for authentication, identity verification, and access to cloud services, while messaging platforms have become essential communication channels. At the same time, security controls that have reduced phishing risk on traditional endpoints have increasingly redirected attacker focus toward mobile workflows, where enforcement and visibility are comparatively limited. As a result, mobile-delivered social engineering has become consistently effective rather than opportunistic.
Attack Chain: iOS vs Android in the Enterprise

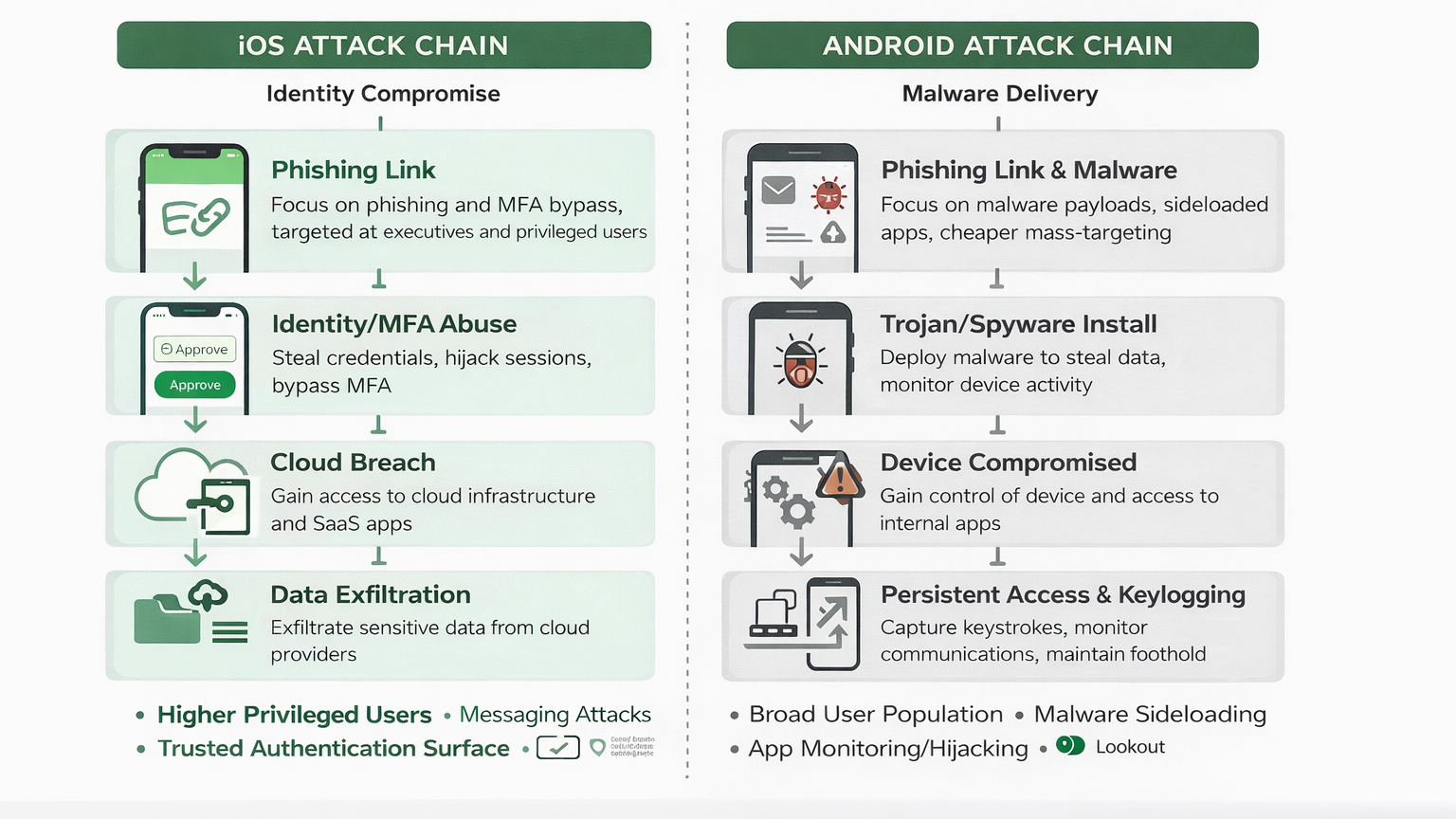
- Enterprise-focused phishing continues at scale, exceeding 1.2 million observed sites in a single quarter.
- Global mobile phishing encounter rates remain consistently high, with nearly 13% of devices affected.
- iOS devices face higher mobile phishing rates in enterprises, not because of platform weaknesses, but due to attackers' tactics. Enterprises often assign iOS devices to executives and rely on them for messaging and authentication while limiting malware attacks. As a result, attackers focus on identity-based social engineering, such as phishing and the abuse of multi-factor authentication (MFA), which offer greater rewards than malware delivery.
- Mobile device management reduces—but does not prevent—phishing exposure, particularly on iOS.
- Mobile malware, device risk, and network threats increasingly appear downstream of phishing activity, reinforcing mobile’s role as an entry point rather than a standalone risk.
These findings reinforce a conclusion that has become increasingly clear throughout 2024 and 2025: organizations without visibility into mobile risk are not just exposed at the device layer—they are blind to the earliest, most actionable indicators of enterprise compromise.
In today’s operating model, mobile signals surface first across identity abuse, credential theft, and cloud access misuse. When those signals are absent, risk is not delayed—it is unseen, allowing threats to progress undetected into core business systems, data, and operations.
This report summarizes our Q3 2025 findings, demonstrating that mobile threats are a significant aspect of modern enterprise security strategy.
Nobody knows the mobile threat landscape like Lookout.

Mobile Telemetry: The Missing Control Plane in the Modern SOC
For today’s Security Operations Center, visibility into mobile risk is no longer optional—it’s foundational. The threat activity outlined in this report reflects a complex reality: mobile devices have become one of the most reliable early access points for attackers seeking to compromise the enterprise through its people.
Threat actors are now weaponizing AI to industrialize social engineering at scale. By harvesting publicly available and organizational data, they generate compelling, error-free SMS messages that create urgency and build trust. Delivered directly to employees’ mobile devices, these attacks bypass traditional perimeter controls and exploit human behavior. One successful interaction—one credential disclosed—is all it takes to pivot into core infrastructure.
Social engineering is only part of the equation. Mobile devices are also targeted through vulnerability exploitation and malware delivery, mirroring—but evolving beyond—traditional endpoint attacks. The result is the deployment of surveillanceware, spyware, trojans, and other covert tools capable of siphoning sensitive data and persistently monitoring high-value individuals, including executives and government personnel.
Legacy SOC operating models were never designed for this reality. Threshold-based response strategies that wait for multiple users or widespread impact fail when a single compromised mobile device can trigger material risk. Mobile-specific threats require earlier detection, greater signal fidelity, and tighter integration with existing SOC workflows.
This report highlights where mobile risk signals appear earliest, what indicators matter most, and how mobile telemetry can be incorporated into existing SOC workflows.
Lookout Threat Intelligence Research Highlights
Mobile Tooling Continues to Mature
Research published by the Lookout Threat Lab during Q3 2025 highlights a continued evolution in mobile threat tooling. Rather than a proliferation of short-lived malware families, researchers observed incremental enhancements to existing capabilities, particularly in persistence, stealth, and data exfiltration from compromised devices.
Across multiple disclosures, common themes included:
- Surveillance and spyware tooling designed for prolonged access, not immediate disruption
- Use of legitimate mobile permissions and services to blend malicious activity into normal device behavior
- Targeting aligned with geopolitical, regulatory, or financial objectives, rather than indiscriminate distribution
These findings reinforce the role of mobile threats as force multipliers within broader campaigns, often operating alongside phishing, impersonation, and account compromise activity rather than in isolation.
Mobile Phishing & Social Engineering: A Stable Threat Floor, Not a Temporary Spike
Mobile phishing and social engineering once again represented the most significant mobile threat category in Q3 2025, both in volume and operational relevance. Unlike earlier reporting periods, which showed quarter-to-quarter volatility, Q3 data reflect a stable, sustained level of exposure across global enterprise environments.

While denylisted and offensive content accounted for the majority of observed sites, the sustained presence of more than 1.2 million enterprise-targeted phishing attacks highlights ongoing attacker investment in impersonating enterprise services, identity providers, collaboration platforms, and internal IT workflows.
Phishing and Malicious Content Attacks by Region
Enterprise phishing and web attack activity varied meaningfully by region in Q3 2025:
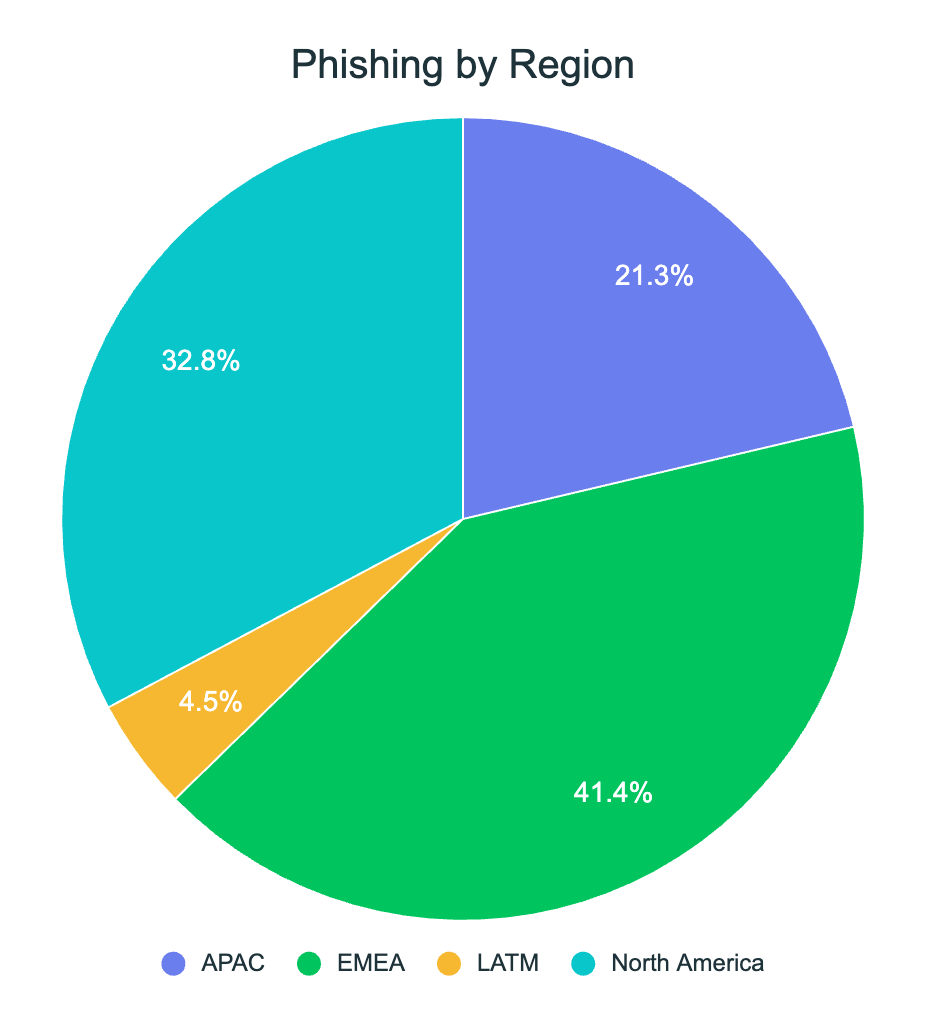
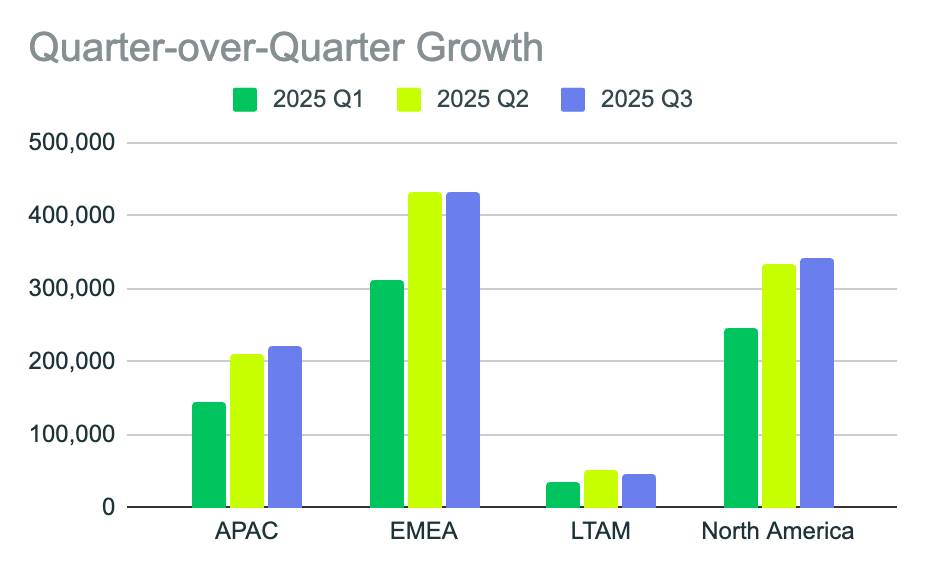
This distribution suggests that while EMEA continues to sustain high absolute volume, infrastructure expansion and attacker growth are occurring fastest in APAC and LATAM.
This pattern is consistent with earlier-stage enterprise digital transformation and rapid mobile adoption in these regions, which attackers increasingly view as high-opportunity environments.
Mobile Phishing Encounter Rates
Exposure Remains Structurally Elevated
Global mobile phishing and malicious web encounter rates in Q3 2025 remained remarkably consistent with prior quarters, reinforcing the conclusion that organizations are operating against a persistent threat baseline rather than episodic campaigns.
- Global Phishing click rate (all devices): 12.88%
- Four-quarter average: 12.86%
Platform-Level Exposure
As observed consistently across previous quarters, iOS devices experienced significantly higher exposure than Android devices:
- iOS: 16.07%
- Android: 7.78%
This more-than-twofold difference reflects attacker delivery strategy and enterprise usage patterns, not inherent platform security differences. Notably, iOS encounter rates increased quarter over quarter, while Android exposure declined modestly.
Managed vs Unmanaged Devices
Mobile device management measurably reduces exposure, but does not eliminate it:
- MDM-managed devices: 12.63%
- Unmanaged devices: 13.61%
Platform-specific differences are more pronounced:
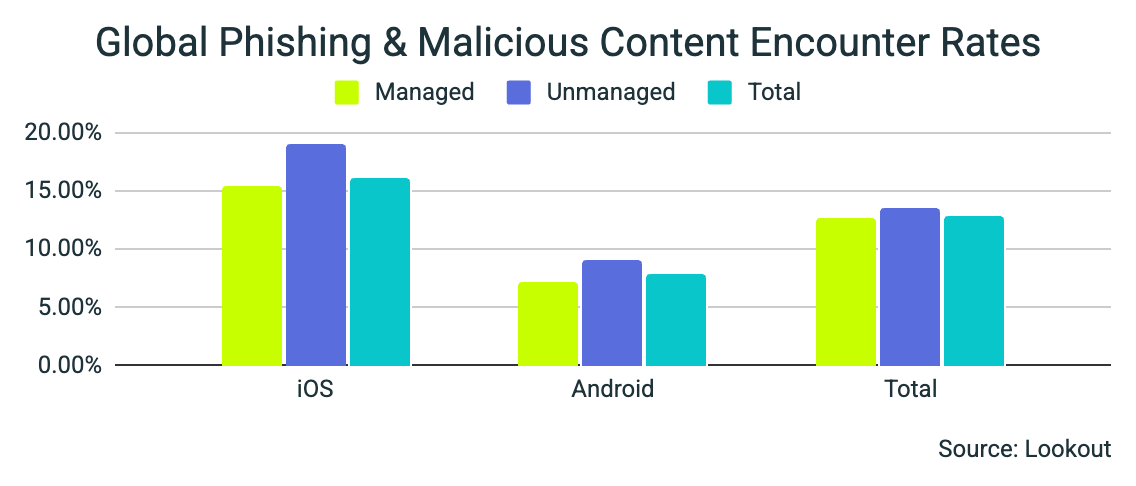
These figures reinforce a recurring conclusion: MDM provides minimal reduction in overall phishing encounter rates but improves baseline hygiene, unless messaging itself is restricted—an impractical option for most enterprises, particularly for organizations that rely on mobile devices for authentication, collaboration, and frontline communication.
Pro tip
Mobile Vulnerabilities
Beyond phishing, attackers exploit human vulnerabilities through system and app vulnerabilities. These vulnerabilities, much like phishing and social engineering, are often exploited via malicious webpages, delivered through similar messaging channels.
Attackers employ zero-click and one-click exploits on mobile devices, leaving security teams with minimal reaction time when employee devices are compromised. Even though known vulnerabilities are typically patched quickly, end-users often delay updates, creating a significant window for exploitation.
Targeting these vulnerabilities is frequently the initial step in a broader device takeover. Once a device is profiled, usually through the delivery of a malicious webpage, the attacker can then leverage the exploit to bypass the browser sandbox, ultimately gaining control of the device or installing surveillanceware.
10 Most Common Mobile Browser Vulnerabilities in Q3 2025
The most common vulnerabilities, when measured by volume across the mobile landscape, are typically in web browsers. This makes sense, as every mobile device has one.
While not all of the vulnerabilities listed below were zero-days at the time of observation, their prevalence reflects delayed patch adoption and the widespread reuse of vulnerable browser components across mobile applications.
MultiApp-CVE-2025-6554
Type confusion in V8 in Google Chrome prior to 138.0.7204.96 allowed a remote attacker to perform arbitrary read/write via a crafted HTML page.
MultiApp-CVE-2025-5419
Out of bounds read and write in V8 in Google Chrome prior to 137.0.7151.68 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page.
MultiApp-MultiCVE-2025-0434-0438
A series of vulnerabilities in various components of the Chrome mobile browser, including V8, Navigation, Skia, Metrics, and Tracing.
MultiApp-MultiCVE-2024-9602-9603
Two types of confusion bugs in the underlying V8 JavaScript and WebAssembly engine in Chrome that threat actors can exploit.
MultiApp-MultiCVE-2024-9954-9966
A use-after-free vulnerability in components of Chrome, such as AI, WebAuthentication, and UI
MultiApp-MultiCVE-2025-4609-4664
Two critical vulnerabilities in Chrome, one of which is a zero-day that was actively exploited in the wild. An attacker could exploit them to leak cross-origin data.
MultiApp-CVE-2024-7971
A type confusion bug in the underlying V8 JavaScript and WebAssembly engine in Chrome that can be manipulated and is exploitable by threat actors.
MultiApp-MultiCVE-2024-10826-10827
Two use-after-free vulnerabilities in Family Experience and Serial components of Chrome.
MultiApp-CVE-2024-12053
A type confusion bug in the underlying V8 JavaScript engine in Chrome that can be exploited via a crafted webpage.
MultiApp-MultiCVE-2024-12381-12382
Two vulnerabilities in Chrome - one type confusion bug in V8 and one use after free in Translate.
Pro tip
Mobile Malware
Mobile malware poses various threats, differing in how they are presented and the data they target. Some exhibit similarities to traditional infostealers, employing tactics like screen overlays, keylogging, and credential compromise to exfiltrate data and facilitate larger attacks. Additionally, app-based phishing presents a risk where malicious apps mimic legitimate sites through webviews, prompting users to log in.
Spyware and surveillanceware escalate these risks by enabling location tracking, data theft, and unauthorized access to microphones and cameras. These threats allow malicious actors to continuously monitor employees, thereby jeopardizing sensitive organizational data and personnel.
This includes detections associated with both newly identified malware families and updates to existing families observed across enterprise environments.
3 Most Encountered Malware Families in Q3 2025
Fjcon
Classification: Trojan
Platform: Android

Fjcon silently establishes a backdoor on Android devices, enabling remote control and the execution of unauthorized tasks that can degrade device performance and further expose the device to compromise.
SequelDrop
Classification: Trojan
Platform: Android

SequelDrop secretly installs and executes additional malicious payloads on Android devices, enabling a remote attacker to control and further compromise them without the user's awareness.
MoneytiseSDK
Classification: Trojan
Platform: Android

This monetization SDK is embedded into applications and offers to turn your phone into a proxy, allowing the developers to make money by routing unvetted network traffic through your device's data connection.

SOC Teams Need to Know Mobile Malware
Mobile threat intelligence is crucial for Security Operation Centers (SOCs) because it fills a critical gap in their visibility, allowing them to understand and defend against the evolving landscape of mobile malware.
By tracking both newly emerging malware families that present unknown risks and updates to existing ones, SOC teams can identify novel tactics and protect against cross-platform attacks, including the mobile components of desktop campaigns and vice-versa.
Given the rise of sophisticated and state-sponsored mobile malware, an increase in iOS zero-day vulnerabilities, and a heavy reliance on mobile social engineering, it is imperative for security teams to prioritize mobile device security and stay informed about the latest threats and attack methodologies.
11 High Severity
25 Medium Severity
3 Low Severity

1 Critical Severity
30 High Severity
49 Medium Severity
15 Low Severity

Malware Classification Trends
Observed malware classifications were overwhelmingly Android-focused, consistent with how mobile malware is monetized and deployed at scale:
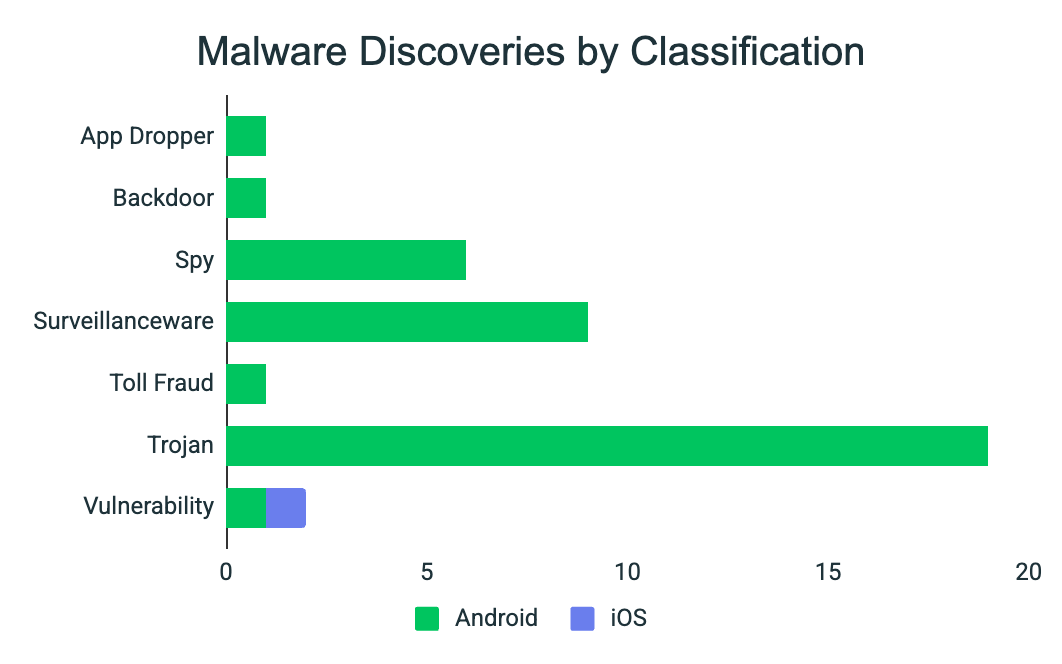
The most prominent categories included Trojans, Surveillanceware, and Spyware, reflecting attacker priorities around data access, monitoring, and credential compromise rather than adware or nuisance applications.
The most critical new malware families of Q3 2025
Of the 39 new malware families detected in Q3, these are the five most critical. Having advanced knowledge of new malware families helps security teams implement proactive measures to defend against them.
AndirSpy
Classification: Surveillanceware
Platform: Android

This application can track user activity and device data and send it to a third party. This includes text messages, call logs, contacts, and more. It can also record video or audio using the device. This can lead to a loss of company data.
Pluton
Classification: Surveillanceware
Platform: Android

This application can steal user data, including text messages, contacts, and call logs. It can also record phone calls. This can lead to a loss of privacy.
Princess
Classification: Surveillanceware
Platform: Android

This application can track user activity on the device and report it to a third party, including text messages, call logs, and contacts. This can lead to a loss of privacy.
CobaltSpy
Classification: BackDoor
Platform: Android

The app is spyware that collects information from victim devices, such as Telegram user account data, by registering user accounts with the attacker's infrastructure and uploading user activity to a remote server. This can result in sensitive information being shared with a third party.
Spylix
Classification: Surveillanceware
Platform: Android

This application is commercial software that will silently track your text messages, call history, contacts, GPS location, and browsing history, and record audio with your device's microphone. It will then upload this information to a remote server.

Pro tip
Device Risks
Beyond threats from phishing, apps, and malware, devices can also be vulnerable due to improper setup. Such misconfigurations expose devices to exploits, potential data loss from physical theft, and even complete takeover.
Top device misconfigurations
Security misconfiguration vulnerabilities can have serious consequences for users. Security misconfigurations can leave a device and its data vulnerable to known and unknown exploits.
Out of Date OS
Out-of-date operating system (OS) versions can leave a device and the data on it vulnerable to known and unknown exploits
Agent Outdated
To ensure protection against the latest threats and access to the latest features, devices must be running the most recent version of the Lookout for Work app.
No device lock
Locking a mobile device is a basic way to secure it. Some users might disable the device lock to make it easier to open their device, which is a security risk.
Out of date ASPL
Google releases Android Security Patch Levels (ASPLs) to patch new and known vulnerabilities in Android apps, Android OS, and even hardware components.
Device Operating System (OS) Threats
While these conditions may represent a small subset of devices, they can materially increase organizational risk when paired with identity compromise or phishing-driven credential theft, particularly for privileged users.
Jailbreaking or rooting a device compromises its security, making it vulnerable to malware and other exploits, and even rendering it inoperable. While some users intentionally do this, malicious actors can also gain remote or physical access to devices, turning them into covert surveillance tools. This tactic is widespread in advanced persistent threat (APT) campaigns, cyberespionage, and state-sponsored attacks
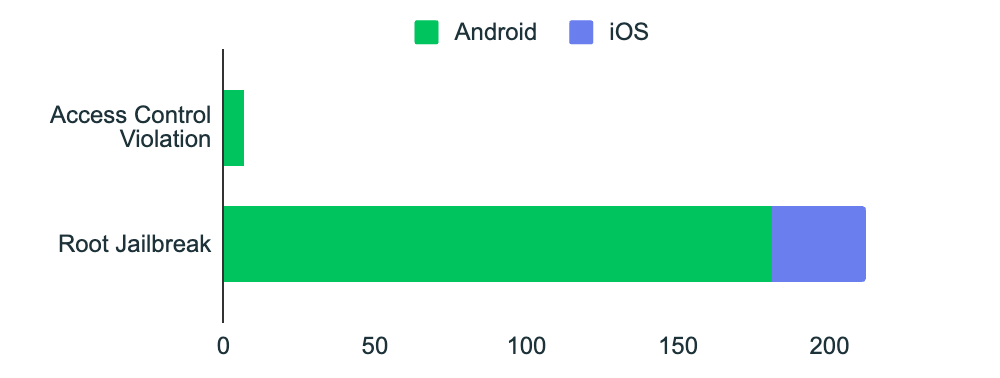
Pro tip
Network Risks
Man-in-the-Middle Conditions Dominate
Network risk telemetry in Q3 2025 was dominated by man-in-the-middle (MitM) conditions, which amplify the impact of phishing and session theft, accounting for the overwhelming majority of observed mobile network risk events.
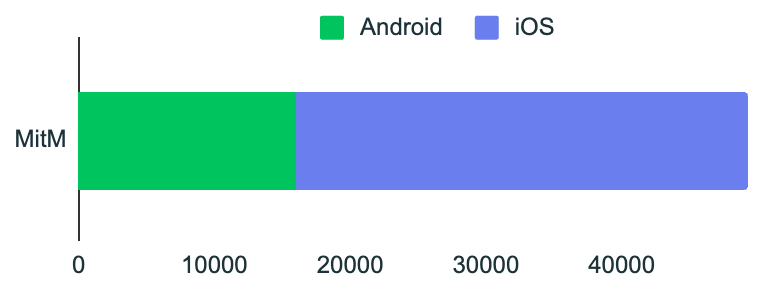
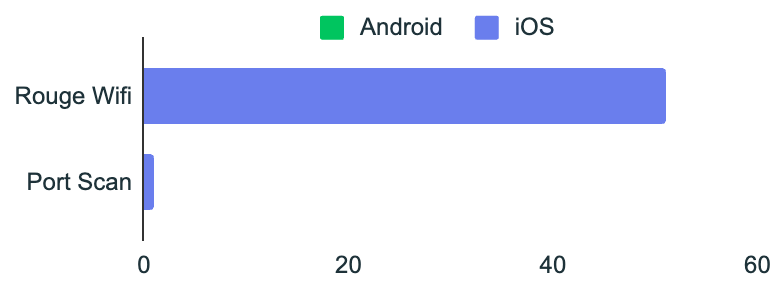
These findings reinforce the role of mobile network risk as a compounding factor, particularly in scenarios involving credential interception or token theft.
Pro tip
Closing Perspective
Mobile Exposure Is Now a Constant
Q3 2025 reinforces a reality that is now difficult to dispute: mobile phishing and identity-centric attacks are no longer seasonal, opportunistic, or peripheral.
With nearly 13% of enterprise devices encountering phishing or malicious content each quarter, iOS exposure exceeding 16%, and more than 1.2 million enterprise phishing sites observed in Q3 alone, mobile has become a predictable and reliable entry point for attackers.
As mobile devices continue to serve as the primary interface for communication, authentication, and access, mobile telemetry has become foundational intelligence for understanding enterprise risk—not supplemental context.

Protect Your Company from Cyberattacks
Find out how Lookout can help you safeguard your business against mobile device cyber threats.

