Executive Summary: Mobile is the Final Frontier
The Q2 2025 Lookout Mobile Threat Landscape report focuses on threats to the front line of modern enterprise organizations: employees and their mobile devices. Even as threat actors shift their tactics and focus heavily on social engineering attacks that exploit human trust and familiarity to gain access to sensitive data, it’s important to remember that threats like mobile malware and vulnerabilities are still critical for the modern enterprise.
Mobile devices are the final frontier of endpoint security. Enterprise employees spend just as much, if not more time on their mobile devices than they do on traditional endpoints. The alarming reality is that despite how critical iOS and Android devices have become to communication, data access, and authentication, many IT security teams think they don’t require the same level of protection as laptops, desktops, or servers.
As groups like Scattered Spider and Shiny Hunters wreak havoc on enterprise organizations around the world, mobile is no longer an afterthought in enterprise security. However, even the most seasoned security professionals might not be totally sure where to start. This report dives into the significant numbers behind critical mobile threat vectors to help security professionals understand what they need to look for when it comes to mobile risk, including:
20% increase from Q1
Consistent with Q1
2% increase from Q1
Utilizing data from the world’s largest mobile security telemetry dataset, the Lookout team is able to uncover significant global trends and emerging threats.
Nobody knows the mobile threat landscape like Lookout.
Mobile Telemetry is Critical to Today’s SOC
Understanding the mobile risk vectors and threatening activity highlighted in this report is critical information for the modern security operations center (SOC). Mobile devices have become the favorite initial target for threat actors who want to compromise an organization via its employees. AI allows threat actors to automate social engineering by crafting urgent, error-free SMS messages based on organizational data, then sending them to targeted employees on their mobile devices. They then convince the individual to share their login credentials, which means it only takes one successful attack for the bad actor to gain access to your infrastructure.
In addition to social engineering, threat actors exploit vulnerabilities and deliver malware to mobile devices just like they always have with traditional endpoints. These instances often lead to the installation of surveillanceware, keyloggers, trojans, and other malware that can exfiltrate data and quietly spy on individuals such as high-level executives or federal agents.
Traditional standard operating procedures (SOPs) in a SOC, which might only look into incidents once they reach a certain threshold of users affected, are not built for these mobile-specific scenarios. This report should help Security teams understand where they need to look and how they can integrate mobile telemetry into their existing SOPs to keep their organization safe.

Lookout Threat Intelligence Research Highlights

Massistant: Lookout Discovers Chinese Mobile Forensic Tooling
Researchers at the Lookout Threat Lab have discovered a mobile forensics application named Massistant, used by law enforcement in China to collect extensive information from mobile devices. Forensics tools are used by law enforcement personnel to collect sensitive data from a device confiscated by customs officials, at local or provincial border checkpoints or when stopped by law enforcement officers.
This tooling specifically was created by Meiya Pico, which provides forensics training and tooling to a handful of risky or even adversarial countries including China and Russia. This can pose risk to organizations that have employees, especially executives, that travel through risky parts of the world. If the country has a policy that allows border agents to collect mobile devices upon entry, as some do, then there is a distinct possibility of a tool like Massistant being loaded onto the device.

DCHSpy: Lookout Discovers Iranian APT MuddyWater Leveraging DCHSpy During Israel-Iran Conflict
DCHSpy is an Android surveillanceware family that Lookout customers have been protected from since 2024. It is likely developed and maintained by MuddyWater, which is a cyber espionage group believed to be affiliated with Iran's Ministry of Intelligence and Security (MOIS). This group targets diverse government and private entities in various sectors, such as telecommunications, local government, defense, and oil and natural gas, across the Middle East, Asia, Africa, Europe, and North America.
In light of the recent conflict in Iran, it appears that new versions of DCHSpy are being deployed against adversaries. It uses political lures and disguises as legitimate apps like VPNs or banking applications. What’s particularly interesting is that one of the lures was a Starlink app, which might make sense considering Starlink was offering internet services to the Iranian population during the internet outage imposed by the Iranian government.

Mobile Phishing & Social Engineering: A Direct Attack on the Human Layer
There are few things that are more directly tied to an individual than their mobile device. In the workplace, these devices are how people stay connected to coworkers, get work done on the go, and in most cases authenticate their identity. We’ve been conditioned to tap into any notification we get – especially when they come in the form of a text message, email, WhatsApp message, or any other sort of direct communication.
It’s also important to remember that employees can reach risky or dangerous parts of the internet on their own. Many organizations have acceptable use policies across laptops and desktops, and they should be extending that to mobile devices. Many do so by taking a proactive approach and blocking access to sites classified under certain risky categories such as gambling or adult content.

Threat actors craft near-perfect replicas of messages that one might expect to get in the workplace, which lead to replicas of login pages that most employees wouldn’t be able to distinguish from the real thing. From there, they’re able to steal credentials and gain access to enterprise data.
What’s more is that AI has made it easier to build highly repeatable and effective social engineering campaigns. Attackers leverage both text and voice to exploit fundamental human instincts such as trust and urgency to increase the efficacy of their attacks.
Managed Mobile Devices are Not Immune to Phishing Attacks
Leveraging mobile device management (MDM) solutions is popular across the enterprise - especially at larger organizations with heavy compliance regulations that issue employees devices for work. MDM is great for controlling which apps are on employee devices, ensuring they’re properly configured, and their OS is up to date. However, they are management solutions and not security solutions. And unless the employer fully blocks all messaging capabilities, which is highly unlikely in today’s age of constant communication, those devices are going to be susceptible to inbound malicious messages.
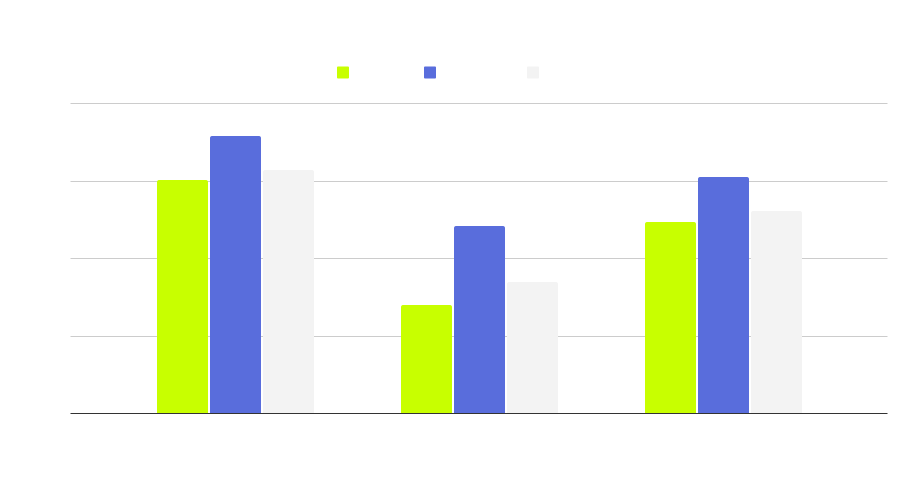
The percentages in the table and graph below represent the percentage of employees who encountered at least one mobile phishing or social engineering attack in Q2 of 2025.
PRO INSIGHT
.png)
The above chart shows how mobile phishing and social engineering attacks vary across organizations of various sizes. While 10% or 15% of your employees being exposed could be an acceptable amount of risk in many cases, but it shouldn’t be in this situation. To put it in scope, 10% of a 7,000 employee organization means that there were 700 unique mobile phishing attacks in that quarter alone. In this scenario where employee credentials and identities are the target, it only takes one successful attack for a malicious actor to gain access to the keys to the kingdom.
Mobile Vulnerabilities
Beyond phishing, attackers exploit human vulnerabilities through system and app vulnerabilities. These vulnerabilities, much like phishing and social engineering, are often exploited via malicious webpages, delivered through similar messaging channels.
Attackers employ zero-click and one-click exploits on mobile devices, leaving security teams with minimal reaction time when employee devices are compromised. Even though known vulnerabilities are typically patched quickly, end-users often delay updates, creating a significant window for exploitation.
Targeting these vulnerabilities is frequently the initial step in a broader device takeover. Once a device is profiled, usually through the delivery of a malicious webpage, the attacker can then leverage the exploit to bypass the browser sandbox, ultimately gaining control of the device or installing surveillanceware.
10 Most Common Mobile Browser Vulnerabilities in Q1 2025
The most common vulnerabilities, when measured by volume across the mobile landscape, are typically in web browsers. This makes sense, as every mobile device has one.
The following vulnerabilities are identified by the Lookout detection name:
MultiApp-MultiCVE-2025-4609-4664
Two critical vulnerabilities in Chrome, one of which is a zero-day that was actively exploited in the wild. An attacker could exploit them to leak cross-origin data.
MultiApp-MultiCVE-2025-0434-0438
A series of vulnerabilities in various components of the Chrome mobile browser including V8, Navigation, Skia, Metrics, and Tracing.
MultiApp-CVE-2024-12053
A type confusion bug in the underlying V8 Javascript engine in Chrome that can be exploited via crafted webpage.
MultiApp-MultiCVE-2024-9602-9603
Two type confusion bugs in the underlying V8 Javascript and WebAssembly engine in Chrome that can be manipulated and are exploitable by threat actors.
MultiApp-MultiCVE-2024-9954-9966
A use-after-free vulnerability in components of Chrome such as AI, WebAuthentication, and UI
MultiApp-MultiCVE-2024-12381-12382
Two vulnerabilities in Chrome - one type confusion bug in V8 and one use after free in Translate.
MultiApp-MultiCVE-2024-10826-10827
Two use after free vulnerabilities in Family Experience and Serial components of Chrome.
MultiApp-CVE-2024-7971
A type confusion bug in the underlying V8 Javascript and WebAssembly engine in Chrome that can be manipulated and is exploitable by threat actors.
MultiApp-CVE-2025-5419
A high-severity zero-day vulnerability in Google Chrome that is known to have been actively exploited. The vulnerability exists within the V8 JavaScript and WebAssembly engine used by Chrome and other Chromium-based browsers.
MultiApp-CVE-2024-5274
A type confusion bug in the underlying V8 Javascript engine in Chrome that could allow attackers to execute arbitrary code on the device via a crafted HTML page.
Pro tip
Mobile Malware
Mobile malware poses various threats, differing in how they are presented and the data they target. Some exhibit similarities to traditional infostealers, employing tactics like screen overlays, keylogging, and credential compromise to exfiltrate data and facilitate larger attacks. Additionally, app-based phishing presents a risk where malicious apps mimic legitimate sites through webviews, prompting users to log in.
Spyware and surveillanceware escalate these risks by enabling location tracking, data theft, and unauthorized access to microphones and cameras. These threats allow malicious actors to continuously monitor employees, thereby jeopardizing sensitive organizational data and personnel.
3 Most Encountered Malware Families of Q2
Triada
Classification: Trojan
Platform: Android

Triada secretly controls the device and exfiltrates sensitive user data to a third party. This can include a variety of data including text messages, call logs, and contacts.
MoneytiseSDK
Classification: Trojan
Platform: Android

This monetization SDK is embedded into applications and offers to turn your phone into a proxy allowing the developers to make money by routing unvetted network traffic through your device's data connection.
WAPDropper
Classification: Toll Fraud
Platform: Android

This malware is capable of automatically clicking on ads. This can lead to a disrupted user experience and increased network usage.

Mobile threat intelligence is crucial for Security Operation Centers (SOCs) because it fills a critical gap in their visibility, allowing them to understand and defend against the evolving landscape of mobile malware.
By tracking both newly emerging malware families that present unknown risks and updates to existing ones, SOC teams can identify novel tactics and protect against cross-platform attacks, including the mobile components of desktop campaigns and vice-versa.
Given the rise of sophisticated and state-sponsored mobile malware, an increase in iOS zero-day vulnerabilities, and a heavy reliance on mobile social engineering, it is imperative for security teams to prioritize mobile device security and stay informed about the latest threats and attack methodologies.


.png)
Most critical threat families of Q2 2025
Of the 26 new malware families detected in Q2, these are the five most critical. Having advanced knowledge of new malware families helps security teams implement proactive security measures against them.
HtmlSpy
Classification: Surveillanceware
Platform: Android

This surveillance tool can forward data such as text messages, contacts, and call logs to a third party. It can also record the device screen and audio, which can lead to passwords being stolen, enterprise data leaking, and private information being uncovered.
GKTracker
Classification: Surveillanceware
Platform: Android

This trojan can record the device’s screen, perform scripted actions on the user’s behalf without their own action, and install additional apps. This can lead to a loss of privacy and/or financial loss.
TriadaFirmware
Classification: Anomalous Firmware
Platform: Android

This trojan can be integrated with apps that appear to be legitimate, but are not. While its main target is financial data, it can also exfiltrate photos and other data off of the device to be shared with unknown third parties.
DevSpy
Classification: Surveillanceware
Platform: Android

This trojan targets user data and financial information by requesting sensitive information from the user and sharing it with unknown third parties. This can lead to account compromise across any work app should the actor choose to target corporate credentials.
RealRat
Classification: Surveillanceware
Platform: Android

This surveillance tool runs secretly in the background and monitors user activity on the device. It collects data such as text messages, contacts, call logs, device data, network information, and more. This data is then uploaded to a remote server to be leveraged against the individual.

Device Risks
Beyond threats from phishing, apps, and malware, devices can also be vulnerable due to improper setup. Such misconfigurations expose devices to exploits, potential data loss from physical theft, and even complete takeover.
Top device misconfigurations
The risks posed by security misconfiguration vulnerabilities can have serious consequences for users. Security misconfigurations can leave a device and the data on it vulnerable to known and unknown exploits.
Out of Date OS
Out of date operating system (OS) versions, especially on iOS devices, can leave a device and the data on it vulnerable to known and unknown exploits.
Out of date ASPL
Android Security Patch Levels (ASPLs) are released by Google to patch new and known vulnerabilities in Android apps, Android OS, and even hardware components.
No device lock
Locking a mobile device is a basic form of securing it. Some users might disable the device lock to make it easier to open their device, which is a security risk.
Unencrypted
This implies that the device doesn’t have a password, pin, biometric recognition, or pattern authentication enabled.
Device Operating System (OS) Threats
Jailbreaking or rooting a device compromises its security, making it vulnerable to malware, exploitation, and even rendering it inoperable. While some users intentionally do this, malicious actors can also remotely or physically gain access to devices, transforming them into covert surveillance tools. This tactic is especially common in advanced persistent threat (APT) campaigns, cyberespionage, and state-sponsored attacks.
.png)

Protect Your Company from Cyberattacks
Find out how Lookout can help you safeguard your business against mobile device cyber threats.

